Every kind of work that demands the usage of a computer may result in inappropriate usage of IT equipment. The end-users – given the opportunity of having a device that apart from working may be used for fun – might be tempted to spend their time more leisurely than they are expected. Yet, nowadays technology provide us with solutions which allow us to monitor computer usage within a company’s server range.
Ethical computer monitoring in work demands to implement a system that is designed in accordance with current law. In European Union, the regulations state that this kind of surveillance cannot be performed in a continuous manner. Such software will be treated as spyware, as it violates an employee’s right to privacy. Because of that, it is worth of purchasing a program which is designed basing on simple, yet tested rules.
Computers that employees work on are the property of the company – because of that, its owner has a right to access the content of computer, and the worker is obliged to show it. Though this situation is clear, it gets more complicated when Internet monitoring and control is taken into consideration.
In case of Internet surveillance, an employer cannot read the content of a website. However, with the use of a system designed to Internet monitoring, gather the information concerning what kind of websites are most frequently visited.
Worktime surveillance will help with depicting how the worker spent his time during the course of work and assess the usage of Internet resources during duty hours.
Internet monitoring is only a part of computer surveillance, though. Printer or external memory drive monitoring, as well as worktime surveillance create a full-fledged picture of how your equipment is used – and is it safe enough to establish an appropriate level of security.
Explore the practical operation of Statlook and uplook systems with a completely free webinar. All you need is a chair, an Internet connection and a web browser.
Controlling computers that belong to your company will let you both gather data concerning Internet usage and enhance network’s security.
With all the data concerning Internet and application usage it will be easy to eliminate the activities that put your company’s network into jeopardy. Software designed to computer monitoring allows you to gather data concerning every activity that worker performed on a computer.
Statlook system enables its user to block undesirable websites which either can be potentially dangerous or used with no accordance to the course of work.
statlook Monitoring is a complex, well-rounded tool to manage IT resources and workers’ performance. It allows to install agents from remote and supports the analysis of workers’ activity with remote employee monitoring while respecting their right to privacy. To ensure the highest level of security, the function of blocking and granting rights on many layers of infrastructure is implemented. It is also possible to monitor comupter from remote places at any time.
Computers that employees work on are the property of the company – because of that, its owner has a right to access the content of computer, and the worker is obliged to show it. Though this situation is clear, it gets more complicated when Internet monitoring and control is taken into consideration.
In case of Internet surveillance, an employer cannot read the content of a website. However, with the use of a system designed to Internet monitoring, gather the information concerning what kind of websites are most frequently visited.
Worktime surveillance will help with depicting how the worker spent his time during the course of work and assess the usage of Internet resources during duty hours.
Internet monitoring is only a part of computer surveillance, though. Printer or external memory drive monitoring, as well as worktime surveillance create a full-fledged picture of how your equipment is used – and is it safe enough to establish an appropriate level of security.
statlook Monitoring enables computer activity monitoring by:
1. Internet Monitoring – this key function enhances workers’ performance while ensuring their right to privacy. The employer may control the usage of company’s network by:
* A list of visited website
* A register of time spent on a particular website
* Surveillance of websites’ headlines
* Surveillance of time spent on certain activities.
The pages may be blocked or unblocked both globally – for the whole company – and locally – for each user. This functionality enables an administrator to limit – or fully restrict – an access to undesirable or dangerous content.
2. Printer monitoring – this issue is especially important if you want to know if the usage of your resources remains appropriate. Unfortunately it happens that some workers use company’s devices for private purposes. Because of that, data concerning printed files – including date and hour of performing the operation, the name of the file, the number of pages and copies, colour and the quality of the printout – are so important to have.
3. Data concerning connected external memory devices – this function protects the network from uncontrolled flow of confidential data. Managing the rights to access the USB memory drives (e.g. blocking, read-only and saving) and saving the activities performed on such devices will grant you a full control on what happens with your data.
4. Detailed analysis of work– with the data concerning breaks of work course, the scope of application usage and logging and session history as an employer you have a full insight on how your subordinates’ workday looks like. This kind of information will help you to assess the productivity of your workers and check if your company’s devices are used appropriately.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.

See our explainer video below:
Software Asset Management (SAM) is a streak of processes which result in gaining a full control over software licenses, thus guaranteeing that the programs are used according to the company’s profit – and in accordance to the current law. It enables you to successfully protect software resources and monitor their usage – which is why it should be a key component for every kind of facility.
As SAM may be treated as a code of behaviour which regulates such aspects as legality of software and procedures that ought to be maintained within every kind of facility, it consists of:
statlook is a professional program designed to control the legality of software. It enables its user to manage the licenses and perform professional audits.
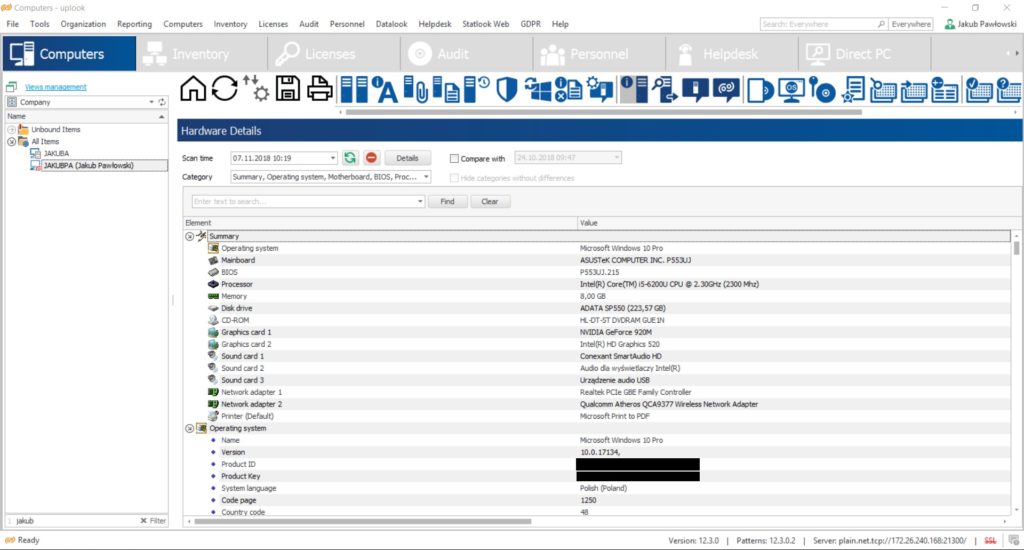
It enables you to audit your company’s software remotely – including multimedia files and fonts – altogether with hardware inventory and servicing analysis.
With statlook, software audit can be performed without forcing the end-users to quit their activities, and without a visible congestion of network paths. This efficiency makes it possible to carry out the audit as often as you need! Both hardware and software inventory – even involving a vast number of workstations – run smoothly and efficiently.
Remote device and software management enables you to perform your tasks without a need to constantly move between locations within the area of your company.
Using barcodes makes it possible to enhance hardware inventory by automation of the whole process – and, in consequence, organize your IT resources efficiently.
With statlook, generating reports basing on every kind of data you may need is simple as never before. The system enables you to define the attributes and parameters according to your preference.
The data are presented in a clear and coherent way – presenting both general and detailed reports regarding any period is no trouble anymore
Ready-to-use equipment and installed software metric templates signed by the end-user who uses the workstation will let you to allocate a certain degree of responsibility from the Administrator to the worker.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.
Now you will be able to limit piracy within your company, thus avoid legal consequences of such behavior. As you may identify the licenses of the software installed on each workstation in no time, there is no possibility of arbitrarily install illegal programs.
With appropriate IT asset management you are able to preciselt derecr akk rge programs installed within your network and make them undergo a thorough inventory.
A detailed set of information concerning possessed hardware and software leads to planning the purchases more resourcefully, thus reducing the unneeded costs and enhancing the effectivity of work. Remember - by organizing the demands for equipment conciously you may reduce the unnecessary moneyspending even by several dozen of percents!
When your company works on several types of software for some reason, SAM enables you to detect and eliminate this obstacle.
A periodical software inventory helps you with eliminating potential dangers. Detailed knowledge about used software and hardware allows you to enhance their security, what reflects in the safety of the whole company.
Explore the practical operation of Statlook and uplook systems with a completely free webinar. All you need is a chair, an Internet connection and a web browser.

Being a branch of IT Asset Management (ITAM), Hardware Asset Management touches upon the issue of hardware life cycle and security. A proper implementation of this IT discipline allows you to:
A professional HAM tool lets you enjoy time-saving by managing your enterprise’s physical infrastructure without leaving your desk. Its main purpose is to centralize the maintenance process, including automating inventory management and keeping your devices up-to-date with ease.
While considering the purchase of such a tool, there raises a question about its most important features. The following description, based on statlook Management feature/suite/bundle, consist a proper coverage of HAM functions, suitable for every company.
It is said that size does not matter – and it comes in par with inventory management systems. The extent of an enterprise should not be taken into consideration, as both smaller and larger ones need a proper HAM deployment.
A properly-designed inventory management software should implement such functions as:
These features let you handle your devices with ease, what consequently leads to a comfortable usage of a product.
Intuitiveness is an attribute that every IT asset management software should not ignore. A quick approach to an information about your company’s devices may fasten your decision-making – thus, improving the course of all of your operations.
With statlook, you are able to create your own database, including warranty and hardware localization. Also, its automatized computer type detection ensures your time-waste is reduced to a minimum.
statlook, due to its technological advancement and intuitveness gains an increasing number of IT specialists' recommendations. By using it, you get to manage your resources from remote, what allows you to take care about more urgent issues. The term "resources" relates not only to acquired hardware, but also other physical possessions, such as furniture, audio-visual components, vehicles, software and licenses. From now, the information about all of your company's possession is at your fingertips.
The process of remote hardware inventory on par with full module synchronisation results in a vast facilitation of your work. No more manual checkout of each workstation. No more impeding end-users' tasks.
Explore the practical operation of Statlook and uplook systems with a completely free webinar. All you need is a chair, an Internet connection and a web browser.
Intuitiveness is an attribute that every IT asset management software should not ignore. A quick approach to an information about your company’s devices may fasten your decision-making – thus, improving the course of all of your operations.
With Statlook, you are able to create your own database, including warranty and hardware localization. Also, its automatized computer type detection ensures your time-waste is reduced to a minimum.
The information about your equipment should be always close at hand. It allows you to take a quick decision on the changes you would like to implement and identify your devices during stocking.
Statlook facilitates this process by:
The more data you gather, the more it needs to be organized. Both virtually and physically, Statlook helps you to manage the flow of information about your hardware.
In order to optimize investments, every enterprise ought to purchase software accordingly to its needs. Implementing both tools for inventory management and software management within one powerful IT asset management software rewards you with lowering the risk of unnecessary money spending. Statlook provides you with both solutions, all wrapped in a comfortable, transparent interface.
A detailed description of statlook system and Hardware Asser Management solution may be found here.
Also, we would like to offer you a free-charge webinar. During its course our programmers describe statlook possibilities while presenting its core actions live. To sign up, please click here.

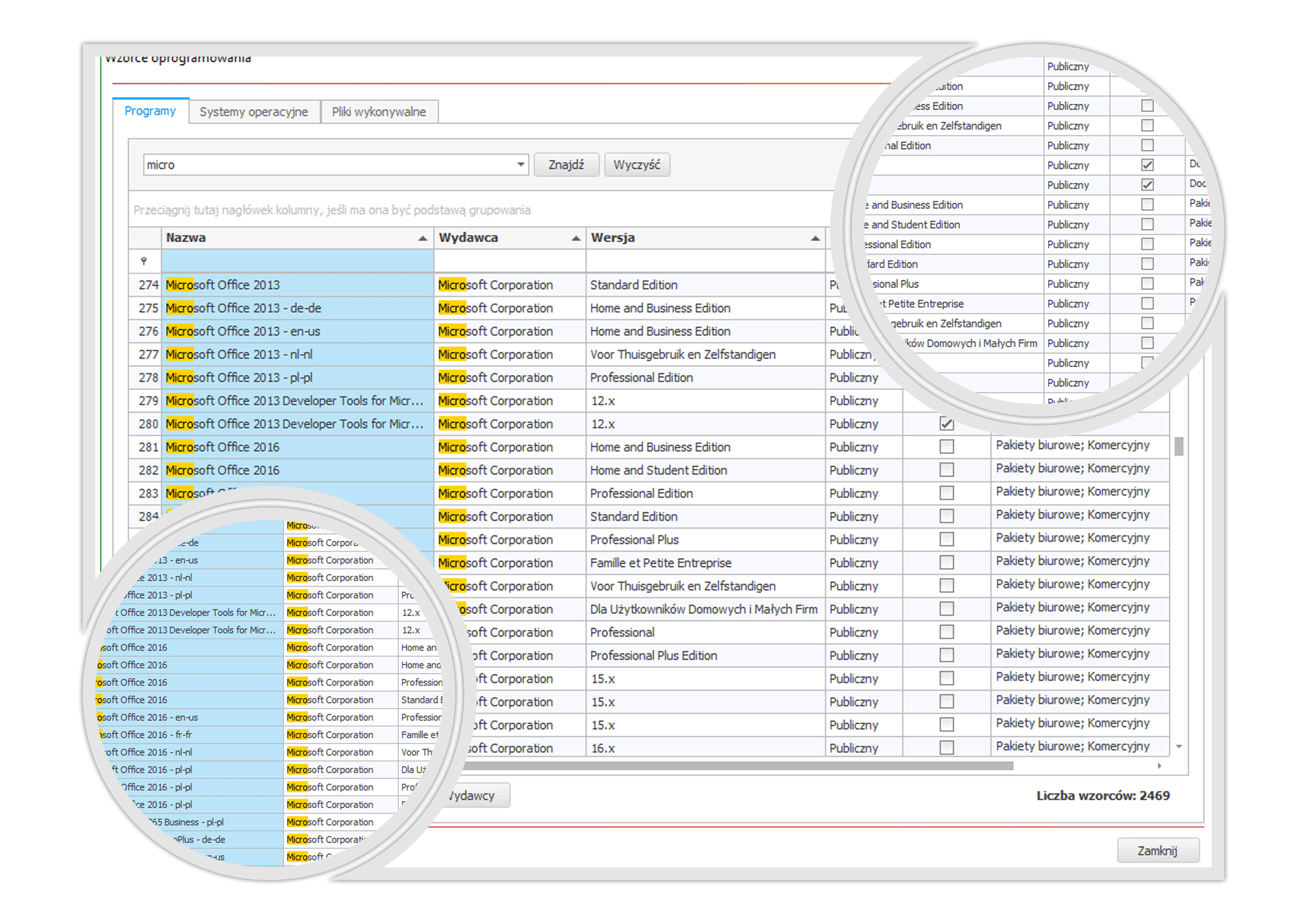
Software Licensing Audit is an element of IT resource management that analyzes the condition of a company’s software, organizing and replenishing the lacking licenses and implementing procedures to enhance software management process. It is addressed to a wide range of companies and institutions.
A standard software licenses audit consists of three main stages:
Software inventory – it serves for gaining a detailed set of information concerning possessed IT resources in a company. Firstly, it is necessary to determine what kind of equipment is used within a company – this includes the number of workstations, servers and OS’s. In the meantime a type of installed software also should be verified. As a result, a detailed report covering the difference between the number of licenses and the data gathered after the audit is generated.
Rescue plan – after generating a comparison report that compares a factual status of possessed software with the number of possessed licenses, the next step is to get rid of each piece of illegal software that happened to appear on the company’s devices. This process also includes unnecessary and unused applications. If a company possesses more licenses than installed programs, they might be installed accordingly.
Creating procedures and codes of behaviour – the last stage describes how to behave with software resources within the whole infrastructure. By implementing those procedures you minimize the risk of installing illegal software – thus, diminish the legality issues and - resulting from them – financial consequences.
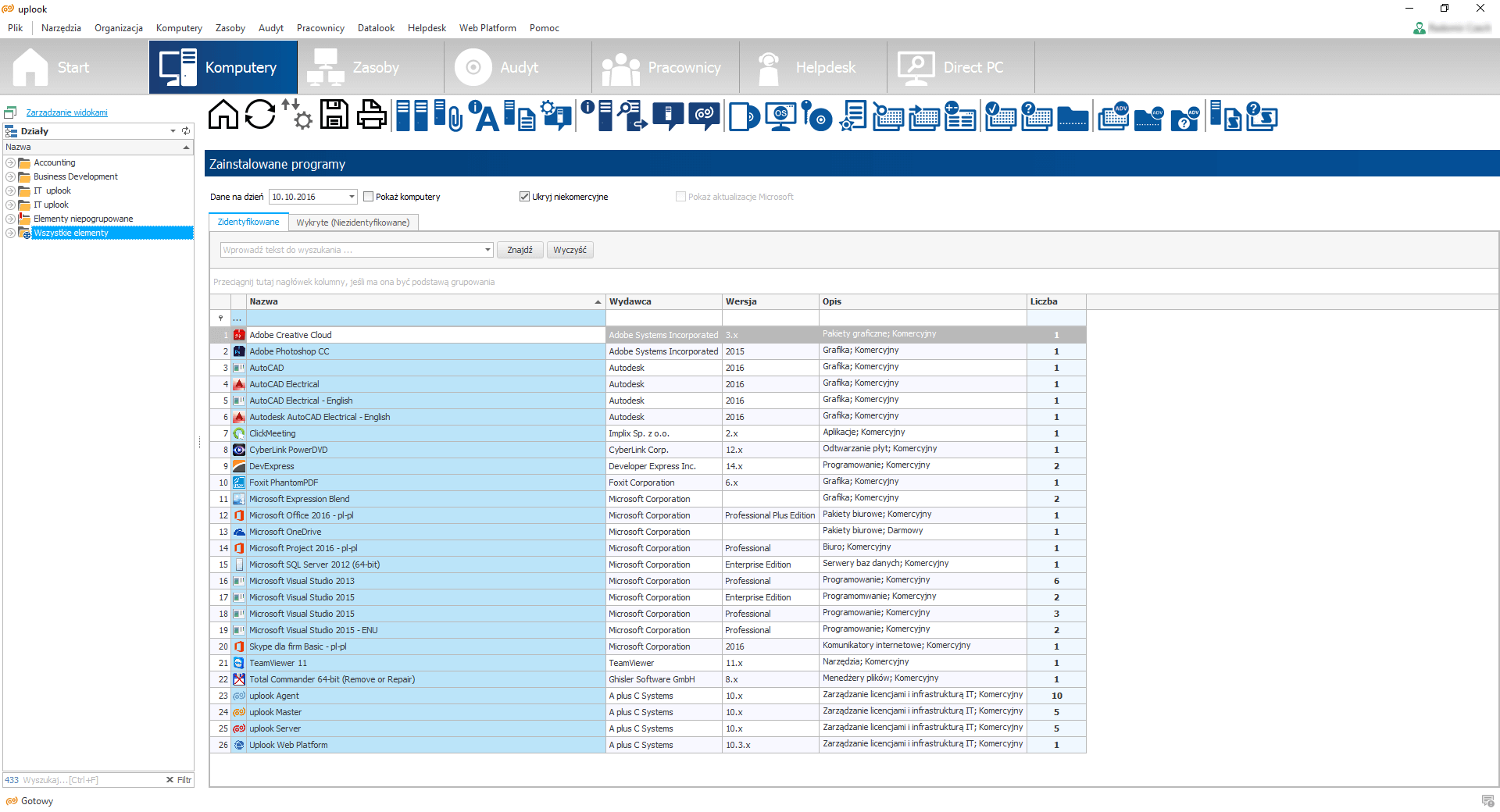
Statlook system is a program serving the purpose of checking the legality of software. Apart from that, it also is a complex system to manage IT resources and control workers’ performance.
Main functions of statlook system:
The issue of software legality becomes more and more important. The law enforcement is increasingly responsive to denunciation concerning possessing illegal programs. As it seems, the decision of implementing current audit is inevitable. It is a burning issue – especially while taking into consideration that your end-users are apt to download and install applications and programs from unknown sources.
Basic aims of performing an audit within the organization are as follow:
Listing programs – in a way that a person responsible for possessed software was sure that each installed piece of software has a license
Checking out if there is a factual need for programs to purchase
Optimal usage of programs by the Users.
Software licensing audit in statlook enables the administrators to easily identify unlicensed programs and multimedia files, and – as consequence – minimize the piracy within the company. Ensuring the legality of possessed software guarantees that your company is secure and will not experience harsh consequences of legal misconduct.
With remote software audit the administrator can perform the whole operation from one place, what vastly decreases the amount of time spent on this activity. Nowadays this is a must in case of such systems – especially concerning companies that use more than several dozens of workstations on a daily basis. With Agents installed on each company’s computer which serve as means of connection between workstations and statlook’s administration console, the audit can be performed without a need to visit each place in person.
It is especially important for system’s functionality which main aim is to save time of IT administrators. The audit might be performed from one place and its results might be displayed later on as detailed, yet transparent reports; tackling the issue individually, by groups or for the whole network. Each audit should be performed in a way that does not disturb others work and prevents the network from congestion.
What are the benefits of performing an audit within a company? First – and foremost – it directs a right course of managing company’s software and prevents us from breaking the law concerning copyrights. To manage our software effectively, we need to gather all the necessary information concerning the licenses – which programs are installed within the network? Is every program licensed? Is every license used? Is every version up-to-date?
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.

As your company grows larger, IT resource management – known also simply as IT management – becomes a necessity. A vast scope of gathered data is especially valuable for administrators, but – besides – it also benefits management department due to transparency and comprehension of presented information.
A key to successful IT infrastructure management is to choose appropriate tools. A simple program to perform software and hardware inventory may not need with your expectations – nowadays, networks become vastly complicated, and the usage of IT resources in everyday work scope might be measured even up to 100%. Each department which needs to use computers must undergo hardware, software and license inventory procedure. Regular IT audit also is considered to be a routine procedure. Besides, it is also important to monitor Internet and computer usage, ensure the security of IT infrastructure as well as manage IT incidents and provide the end-users with remote helpdesk to support their everyday work.
IT administrators who struggle every day to keep the whole IT infrastructure working could find it vastly troublesome to perform successfully without a well-rounded IT management tool. Such a system needs to provide him with automation of certain processes, be in accordance to the current law and employee rights and be coherent and simple to work with.
An IT network is not only workstations and laptops – it also includes routers, switches, phones and computer components. It is crucial to pay attention to what kind of details you may gather while conducting an inventory with the usage of your IT resource management system.
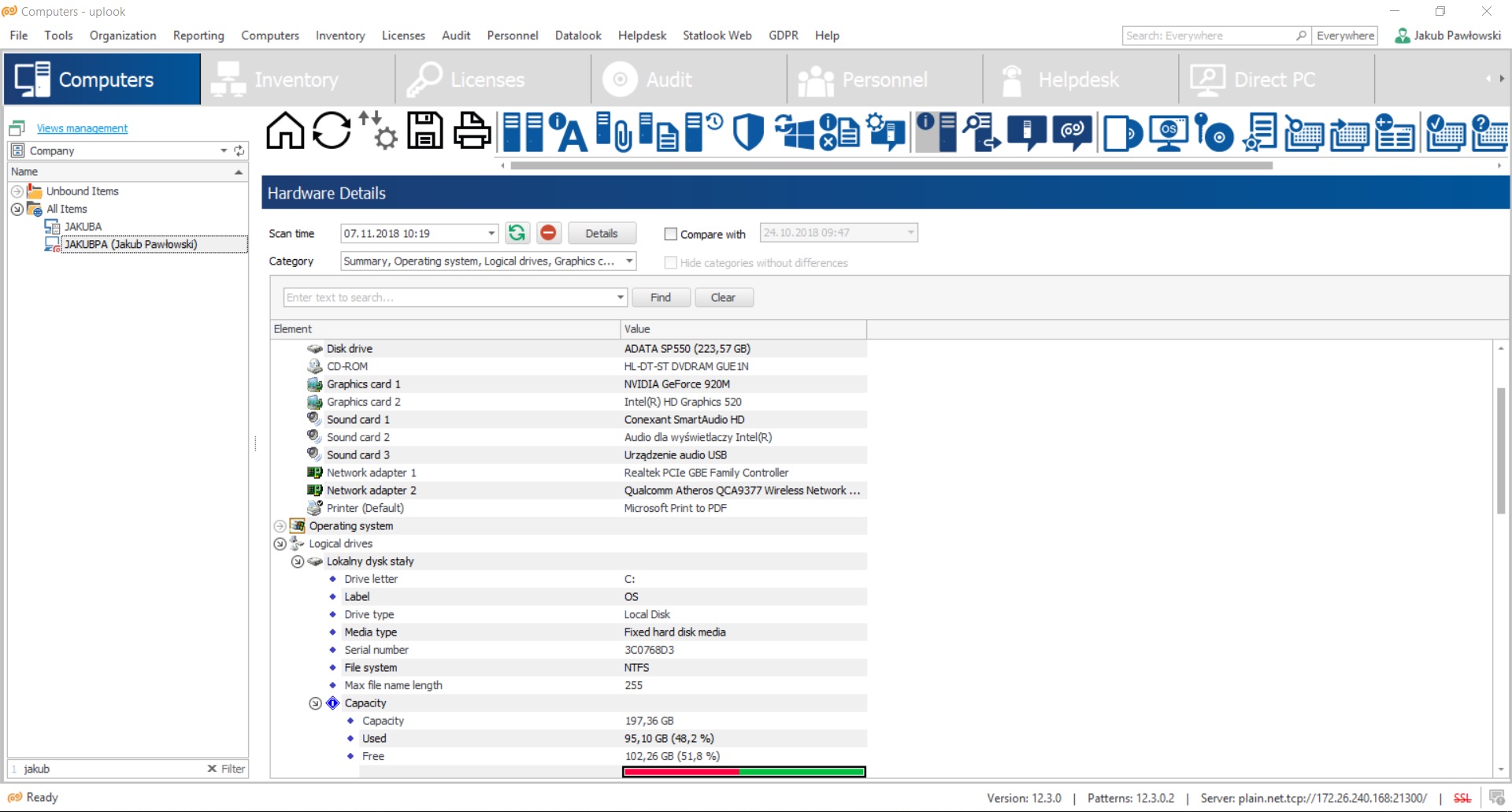
License manager is another component which ought to be a part of your company’s network management system. This kind of tool should detect all the licenses automatically – no matter if commercial or not. Because of that, it also ought to be equipped with a recognition pattern database which updates automatically. Besides, an appropriately – designed software manager should monitor the changes of licenses’ status on a current basis – in accordance to their type, date of expiry and producer.
A software license audit is a part of IT audit which can be performed autonomously. While choosing a software to manage IT infrastructure it is worth to check if such a program possesses functions allowing to conduct an internal software legality control concerning suites, programs and applications. It is also important to an IT administrator to ensure that the changes within installed software are under constant control and that an unauthorized software installation is detected.
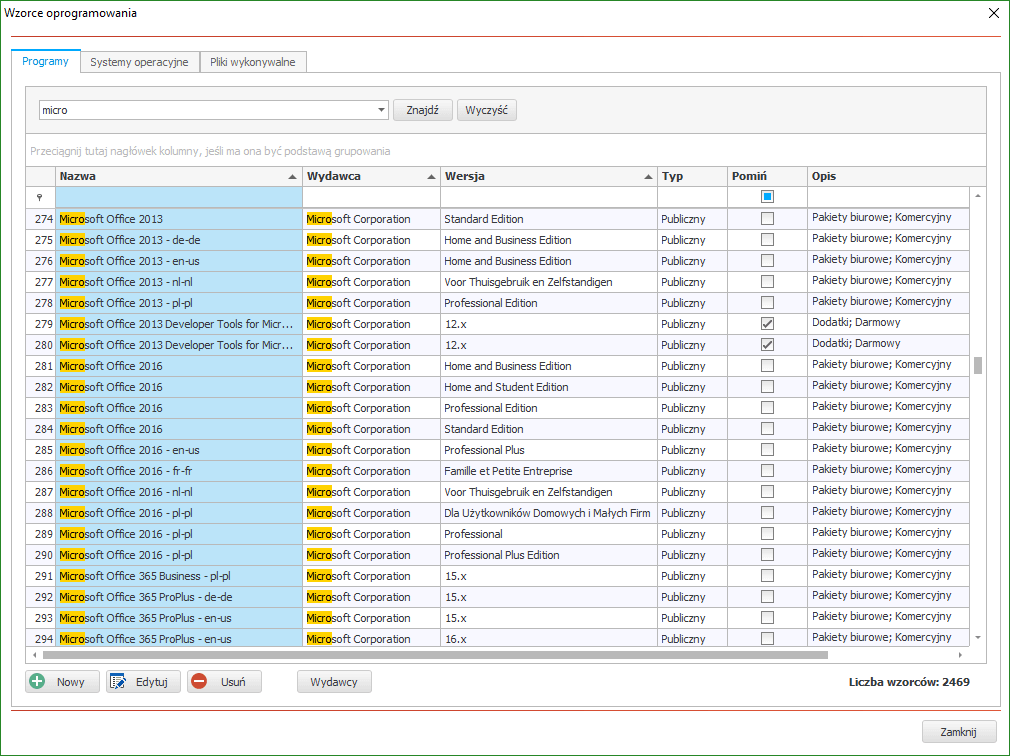
Computer and users monitoring is also an important part of network management software. A key component of such a program is to have a register of users’ login sessions, as well as launched applications, visited websites, installed software and opened files or multimedia. It also should include data access management and blocking undesired websites and applications. What is important – each function should be designed to be in accordance with the current law that a company should bide to.
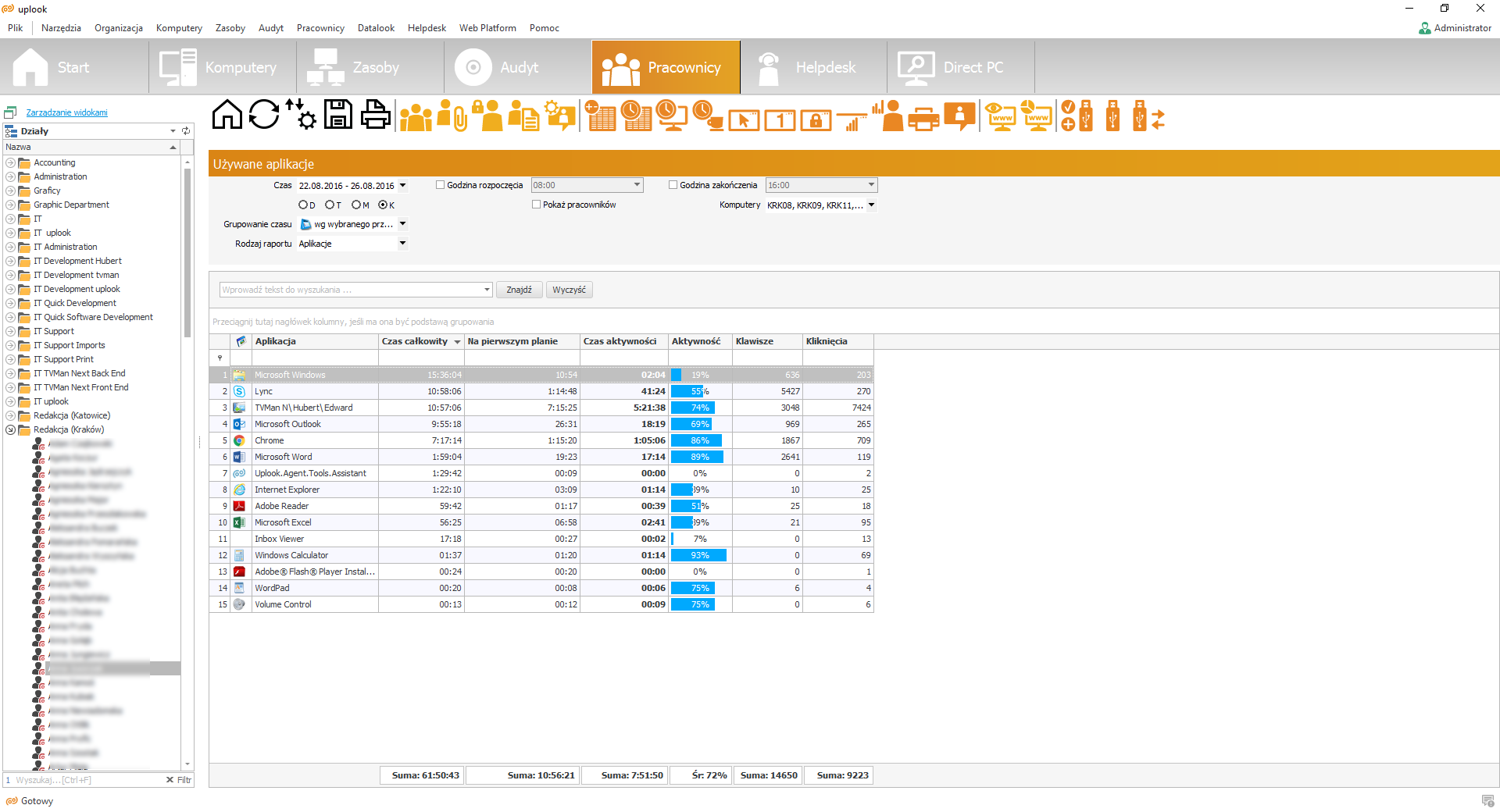
Another element which should be paid attention to is a possibility of monitoring the operations on external memory drives and printer control – including web and virtual printers. It is important for such a program to block the rights to save and read from USB devices and allowing to authorize their usage.
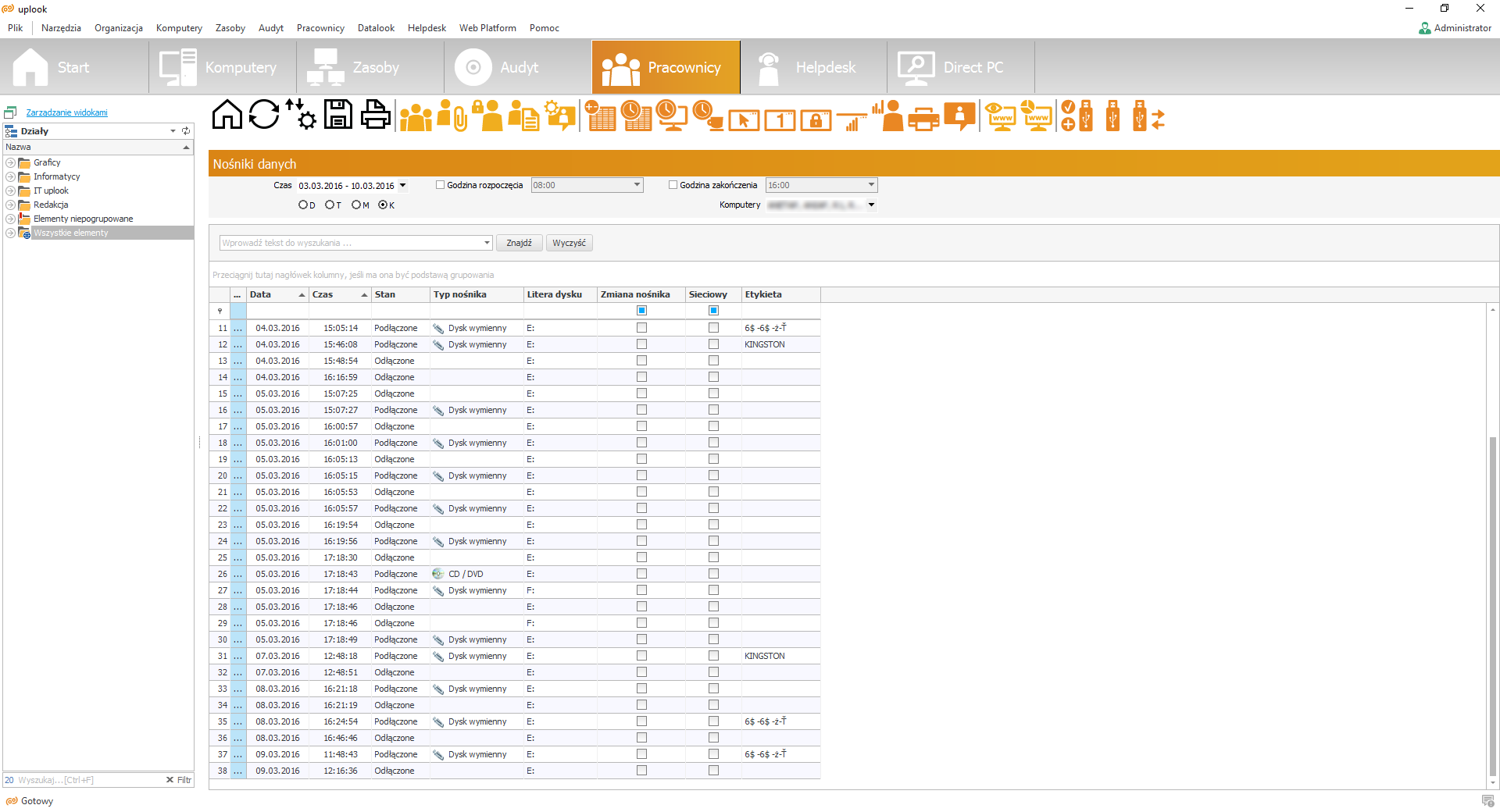
IT infrastructure management also demands providing service to IT-related incidents. A properly-designed helpdesk system should include a possibility of receiving notifications from end-users automatically and ascribing tickets to workers responsible for solving such an issue. Both a user and an administrator should be provided with an option of adding a comment, attachments and printscreens to a person responsible for IT service. A central knowledge base is also important to have – as you can follow incident history and see how to solve similar issues.
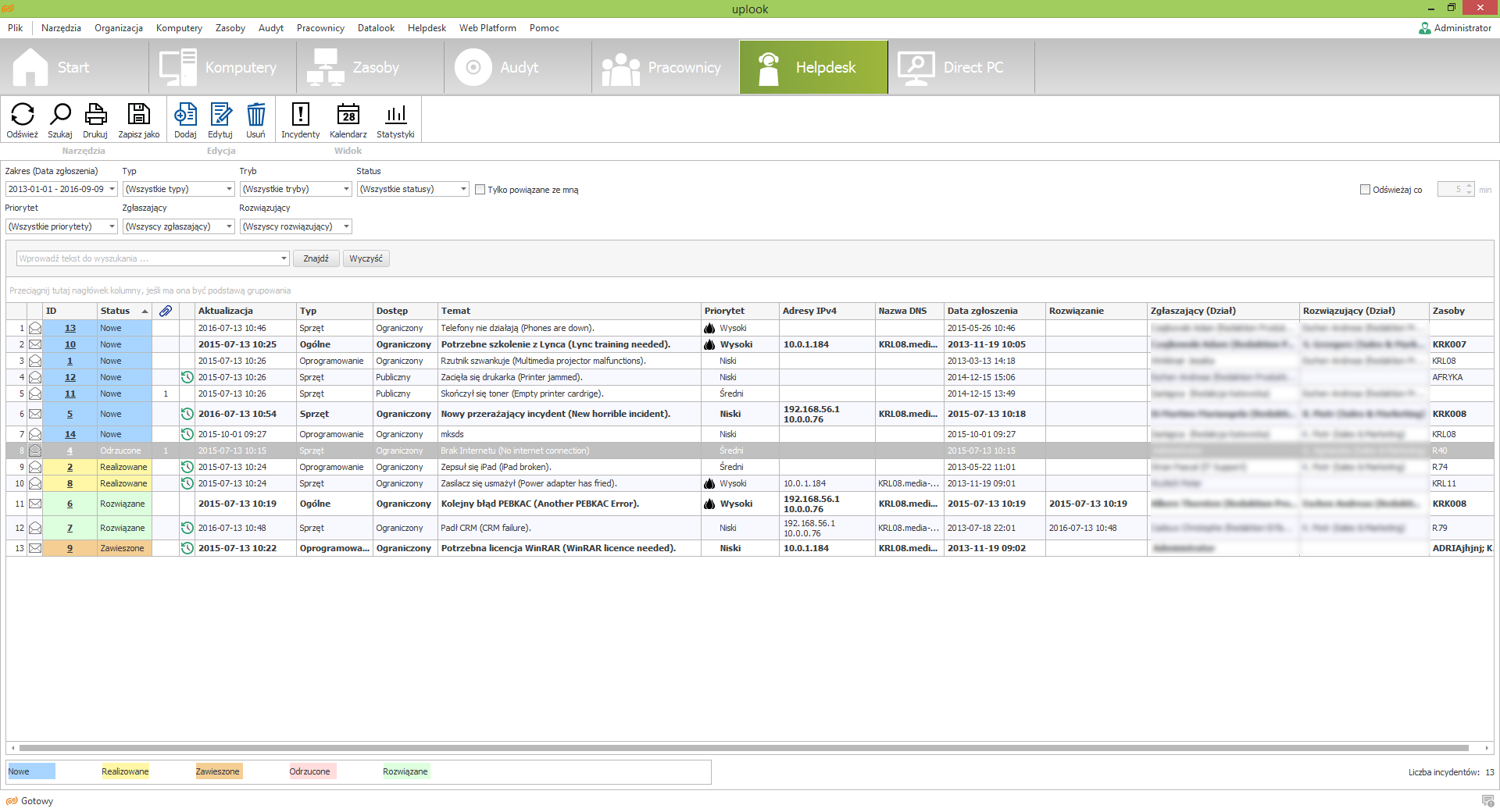
An immediate help to end-users through a remote connection is a key component for every IT management system. A good software should consist of an option to connect to a user’s dekstop remotely and perform operations on his files and catalogues. It is important for an IT administrator to preview several desktop simultaneously.
Implementing one, many-faced system to manage an IT infrastructure may result – first and foremostly - in cutting time expenditure. All the knowledge about the network is visible through one intuitive application. A management console allows you to perform a necessary action immediately – without a need to communicate from one place to another or changing a program to launch certain option. Moreover, one system means lesser money spending – instead of buying plenty of programs which functionalities are often not adaptable you can buy a well-rounded one which suits your needs.
Statlook makes IT administration more efficient and coherent.
Statlook is a professional solution to manage both IT infrastructure and workers’ performance. With controlling your employees’ worktime activity and working hours registry makes it easier to perform human resource management tasks and enhance your company’s overall performance. Statlook equals a full range of knowledge about the activities done on computers that are connected to the company’s network.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.

Throughout the years, the process of software assess has become increasingly difficult. This happens due to neglecting proper license management practices, one’s inability to control software investments and complex structure of software licensing agreements. The fact that companies progressively decide to use cloud technology does not make this situation easier to handle. Because of those reasons, most companies struggle to be compliant with their license agreements.
Apparently, there exists a solution – purchasing a professional compliance management software. A well-rounded, efficient system ought to possess several functions, which enable your IT administration to handle this issue properly. The further description, based on statlook Asset Management feature, touches upon these aspects and describes how to create a neat, safe environment for your licenses.
The process of license auditing ought to be performed continuously – providing that, IT administrators can constantly be switched on legal policies of your software. In order to understand the complexity of license compliance manager’s task, one should address several issues:
With remote application search and remote file search options, statlook facilitates your work with possessed software. Keep in touch with obtained programs in any time, any place.
It just takes one USB hard drive with an Agent installed to scan your computers manually. Do it however you want – the result will be satisfactory nonetheless.
Put programs in order according to their functions. Assign their licenses with software patterns with License Manager. Track and identify your company’s software like never before.
Some people believe that there is a kind of order in chaos. However, this cannot be applied to license compliance process. With statlook, your software register can be neatly arranged, what allows you to control it with ease.
The features mentioned above provide you with both financial security and assure you that there is no legal risk due to possessing outdated license in each of your estates. In the age of cloud computing, automation is a key to prosperity – and this applies also to license compliance. Statlook not only provides you with that, but also compounds other features, including monitoring and resource management, thus being a comfortable, efficient system which covers most of functions necessary in every company.
More information about statlook system may be found in a detailed description of the functions here: https://www.statlook.com/statlook
Explore the practical operation of Statlook and uplook systems with a completely free webinar. All you need is a chair, an Internet connection and a web browser.
MUI application is designed to and carry inventory and manage IT resources from your mobile devices. They have already been recognized as extremly useful tools in everyday IT-administrative work.
These functionalities now reach another level of usability, as they introduce new features and intuitive interface on every platform you may use. MUI is compatible not only with Android and Windows Phone - now, iOS is also an option!
The simplicity of usage has always been our motto, and in case of MUI we reached the peak of intuitiveness. After installing the application, the user ought to insert appropriate credentials and uplook server's IP address. By doing so, the access to devices registered in statlook system will be established.
This solution comes in handy especially for administrators who work "in-field", within multiple localizations and those who maintain the technical issues of company's devices.
.
Imagine that a worker reports a problem with a serious computer damage. Most frequently, an administrator has to go the workstation and - first of all - identify the damaged device. Usually, it proves to be difficult - especially if the damage causes the computer to be unaccesible.
Because of that, these seemingly simple questions may appear to be very difficult to answer:
Accessing such information in certain facilities is often difficult, as it demands consultation with another departments, e.g. the accountancy one. It is a vast nuisance, as it takes your valuable time, which could be used to deal with other important tasks. Mobile Uplook® Inventory allows you to check all the necessary data concerning both the devices and their incident history much quicker:
Using Mobile Uplook Inventory saves your time while handling servicing requests. It comes in handy especially if you are working within multiple locations. Yet, it also is an invaluable asset in case of smaller companies, as localizing and identifying a computer also can appear to be a difficult task to do. Altogether, using MUI will influence the profitability of IT departments, thus accelerating the return on investment in statlook system.
Mobile Uplook Inventory visibly enhances the comfort of work for both IT administrators and managers. A constatnt accessiblity to most crucial data about IT infrastructure via mobile phone is a must for many administrators. MUI application is one of the factors that highlights A+C systems from other Polish IT Asset Management systems' producers. None of them offers such a variety of possibilities.
The application can be downloaded for Android, Windows Phone and App Store. Enter its name to the browser below and download an appropriate version.
Software licenses are assets and investments and should be managed as such. SAM helps you control costs and optimize these investments as your organization evolves.
Software Asset Management (SAM) is an industry best practice that helps you control costs and optimize software investments across your organization and throughout all stages of their life cycles. Administered through an ongoing plan, SAM makes it easier to identify what you have, where it's running, and whether redundancy may exist. A fully implemented SAM plan can help you cut costs, improve security and compliance, and also anticipate future software needs. SAM also helps organizations accurately capture the costs and benefits associated with IT projects that enable a competitive advantage.
If your business relies on its IT operations to operate smoothly and efficiently, you are probably well aware of the complexities of managing software across an entire organization. What is the best way to control costs and manage business and legal risks? Could you do more with the software you already have? Will your current IT infrastructure be able to expand as your company grows?
SAM is a proven industry best practice of business and IT processes and procedures combined with technology that can help your organization:
| Control cost and business risk for a stronger, healthier financial position. |
Optimize existing software investments, to enable you to do more with what you already have. |
Grow with your company's expanding needs through a core foundation with increased flexibility and agility. |
SAM can help you control both the "hard" monetary costs of software and the "soft" costs of IT management. It helps ensure that you have the best licensing programs for your organization’s specific needs, and the most effective IT forecasting and budgeting. It can help you centralize your IT and software asset tracking, automate manual processes for increased efficiency, prepare for technology upgrades, and reduce support costs.
SAM can also help you control business and legal risks that are often related to improper software deployment. Use SAM to identify security vulnerabilities and keep track of the latest software updates, as well as achieve compliance with standards and government regulations.
With SAM, you can get the most out of your software investments by reducing redundancy, standardizing processes, and giving your employees the tools they need. SAM can help you implement IT with business best practices and optimize software assets, enabling you to pay only for the software you use. SAM helps you optimize IT resources by standardizing processes, improving automation, and defining procedures to increase the efficiency and agility of your IT staff.
As your company needs grow, you need an IT infrastructure that can expand with you. The SAM optimization model provides a solid, scalable foundation for business growth. A fully implemented SAM plan creates efficiencies that enable you to adapt quickly to market opportunities, plan for future software needs, and engage in IT and business best practices that drive value. At its highest level, SAM helps organizations become more agile by making better use of resources, even in times of changing business conditions.
The goal of Infrastructure Optimization (IO) is to build an efficient, secure, and optimized IT infrastructure. IO can help your organization better understand and move toward a more secure, well-managed, and dynamic IT infrastructure that will help you reduce costs, use resources more efficiently, and make IT a strategic asset for the business. IO is a four-step process that can take your organization from a non-managed, reactive state to a proactive, optimized, and dynamic state. SAM is a key step in IO that can help your organization gain control over what IT assets are being used and where.
Source: Microsoft/SAM
Experience firsthand how Statlook AI revolutionizes IT management with its comprehensive features and user-friendly interface.