
Every company or institution that vastly depends on computer and Internet usage demands a certain level of IT security. First and foremost you need to take care about malware, hacker attacks and data leakage. Most of the companies is aware of the importance of such precautions – especially due to the experience of IT administrators who recommend implementing a system to wide-angled IT resource management which includes a tool to control users’ activity on the Internet.
This includes information concerning: visited websites and domains and multimedia and software that was downloaded through this connection. Uncontrolled access to Internet puts the whole company into a danger, as the administrator is unable to quickly identify and eliminate the source of a problem.
Implementing an Internet surveillance system will facilitate the process of identifying a danger. Systems such as statlook not only enable you to currently monitor the actions of end-users – they also provide you with the option of blocking undesirable websites and files loaded on it, what will prevent any kind of dangerous situation.
During the course of work, the Internet ought to serve as a tool to perform daily duties. Using it for private purposes or for fun does not correspond with labour code. This phenomenon is known as cyberslacking and, unfortunately, appears worldwide.
This phenomenon applies to over 70% of all workers (according to the research performed in 2008 by Geminius company). 46% of the subjects declare that – apart from the breaks – they spend around half of hour while surfing on the Internet on a daily basis. It means that one worker spends around 10 hours monthly on activities that are not work-related. If we multiply this number by the number of workers within your facility, the result will appear to be alarming – especially while taking into consideration the fact that the statistics concern only the half of respondents.
Implementing a system designed to Internet control will limit the loses are caused by cyberslacking.
“The possibility of getting such data as register of visited websites, opened documents, launched applications and many other detailed pieces of data that concern the activites performed during the workcourse has a positive impact on workers”
– states the Head of IT Department of National Forest Holding "State Forests”, who remains to be our client.
The Internet is not only a useful tool to work – it is also a source of potential danger, usually caused unintentionally by the workers. The information about entering a dangerous website or downloading a program from an unknown source too often is delivered to the IT department after infecting the whole network. Media are overflowing with the news concerning data breaches caused by viruses downloaded from unchecked websites.
One of most famous cases concerning such an issue was Virut. At least three million of IP addresses worldwide were infected by a virus known as Virut – as described by the report published by CERT Polska team, which works within NASK Research Institute. The virus - which was spread through websites – was used to distribute spam, stealing data and perform attacks through DDoS.
To protect your company’s network from this kind of danger it is not enough to implement Internet monitoring. The key function of a complex, well-round system is to block websites and domains as well as access to multimedia on the level of the whole organization. Statlook system is equipped with such functionalities – you may block a certain web address both globally and locally. Preventing the danger costs less than dealing with consequences.
Monitoring suite is a part of statlook system – a complex tool to IT infrastructure management. To get more information it takes only to download a demo version or take part in a free webinar, during which the functionalities of our system are presented live.

Controlling and assessing worktime is a law-regulated duty of every employer. Labour law is very strict in this matter – worktime registry is a basis to make financial statements and underlying accounts. It does not matter how many people work under us – worktime registry should be done before channeling wages.
Many companies does not respect that duty thoroughly, basing on an assumption that every worker respects the code of behaviour – thus, every worktime break or holiday is applied in oral or written form to supervisors. It appears, however, that this is not the best solution. The employees often forget to report pieces of data which are key for their employer.
The answer to that problem is to implement a coherent work surveillance. Below, you have listed several important aspects of worktime registry:
An appropriate solution to this issue would be implementing a tool to control the employees’ worktime performance. Such systems deliver a thorough information on an actual worktime activities, breaks, planned vacations and sick leaves. Moreover, workers have possibility of checking their own statistics and assessing their worktime on their own – including worktime schedule and actual work effectiveness.
Worktime registry should include the number of hours spent on work on a daily basis, which includes:
– Overtime payments
– Saturdays and Sundays
– Remaining public holidays
– Vacations
– Sick leaves
– On-call times
– Excused and non-excused absences
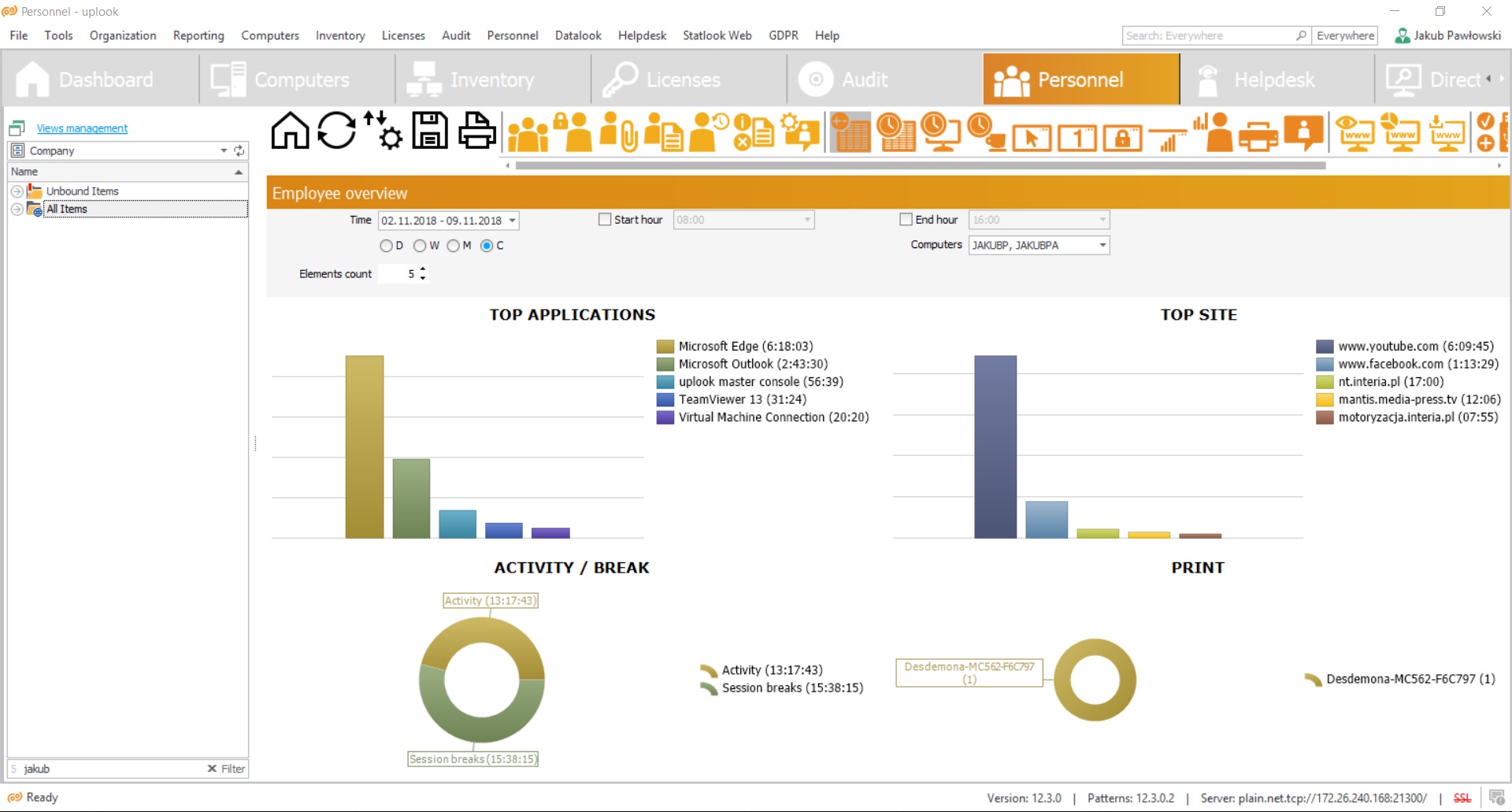
Statlook enables a worktime control by providing valuable information concerning used applications, websites, activities and worktime breaks.
Maintaining a registry can be done with IT tools in order to automat it. Because of its simplicity and highly advanced technological solutions, statlook enables administrators to easily, yet thoroughly check the software installed within a company.
Statlook is equipped with a unique technology of conclusive application detection. What makes it more interesting, it is not vulnerable to your employees’ ‘tricks’ who may try to hide illegal applications.
With only one tool a company’s owner may rest assured that he keeps everything in order. System assesses the course of work automatically – for each worker separately. The data are presented as coherent reports, which can be printed or saved in any format according to your needs.
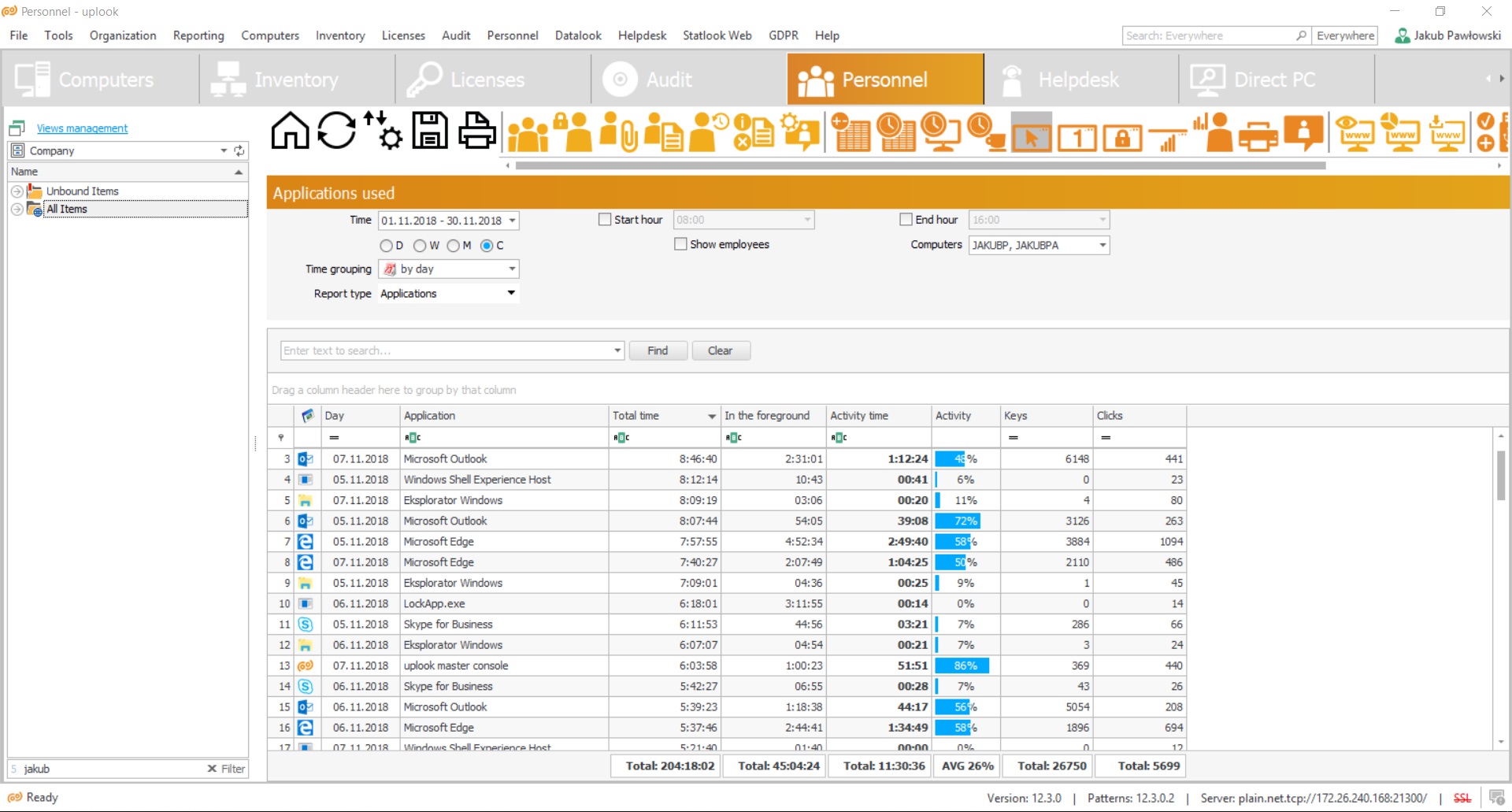
The screen below presents an example of worktime assessment.
Maintaining a register on paper is uncomfortable and ineffective. To enhance this process, use tools designed to control and assess the worktime performance:
– receiving reports from a worker about tasks done during a day or week
– current worktime monitoring and control – especially valuable for an employer who is obliged to do it by law
– entering data concerning every worker – including positions, departments, the scope of responsibilities etc.
– checking data concerning the number of hours spent on work – statlook counts worktime periods from logging in to logging out
– preview on programs, applications and opened files used during the course of work
– Generating reports basing on personal worker cards – no need to input the data manually
Software registry is a key element of every professional software legal audit. It bases on creating a detailed set of data concerning software as well as controlling the course of installating programs on computers within the company’s network. Only by mainaining such a register and control will guarantee that you have a thorough knowledge about possessed software and will allow you to put them in order, get to know how many licenses you have and implement appropriate procedures concerning software management.
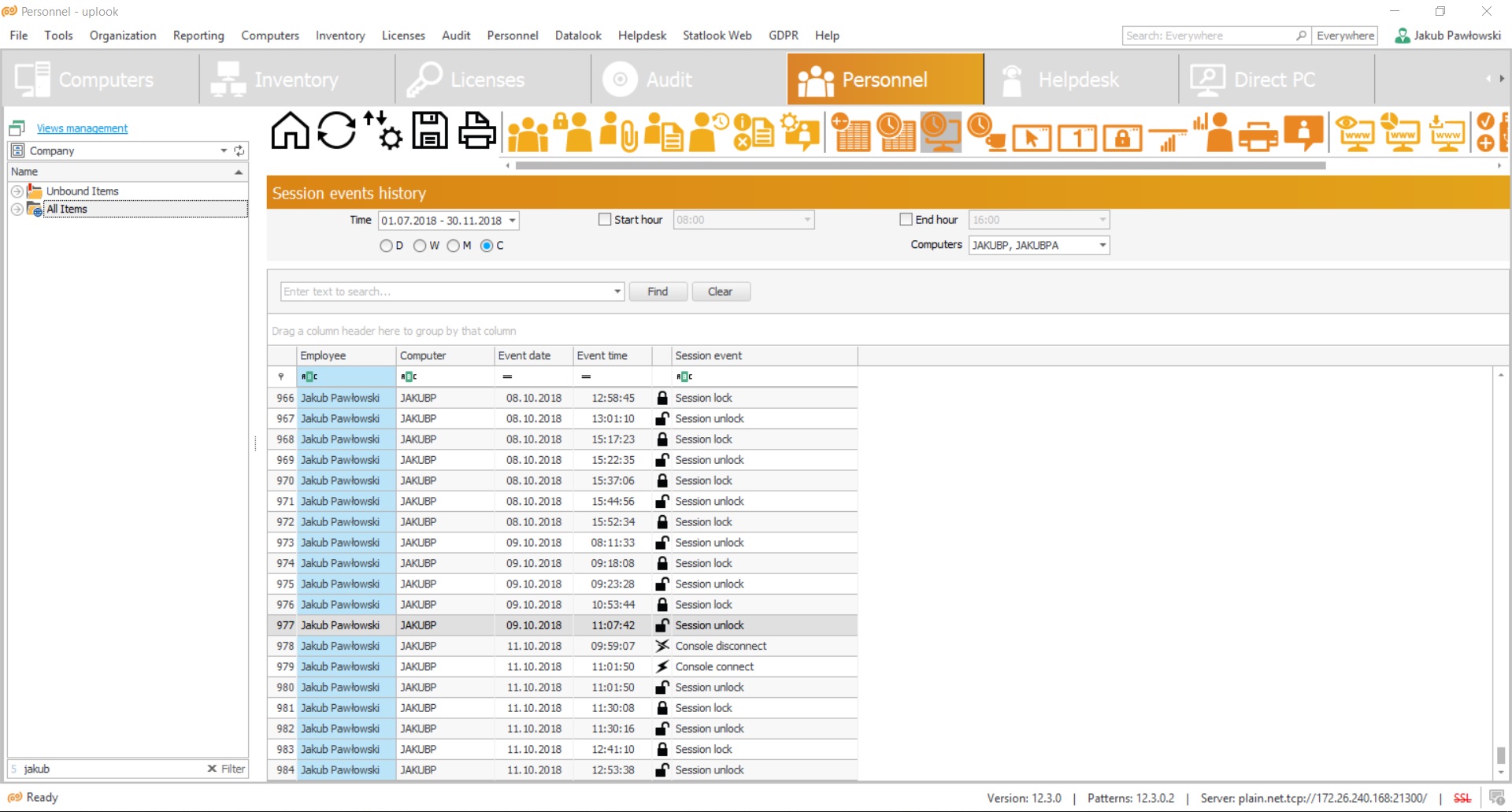
The mechanism of disc scanning is enriched by a function of scanning archival files. There will be no possibility of hiding anything – no matter if by changing the name of a file or compressing them within .zip or .rar format. It enhances the plausibility of maintaining the registry even more – thus, enables you to grasp full control over audit and your company’s security.
Apart from counting time of work and breaks, our system also monitors the activity of the workers who spend most of their time in front of computers. User acitivty monitoring is a part of system that enables a manager – or an owner of a company – to check what kind of applications, websites and files were used during work. This will allow you to appropriately assess the quality of their work. These data are gathered automatically – after logging in the agent sends all the necessary data on a server. Because of that, worktime control is much easier and more comfortable.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.

Nowadays, each sector has to take into consideration a rapid development of IT industry – and this includes a banking sector. The computerization of financial service is beneficial for both business and consuments. It is worth to remember, though, that global computer use development may endanger your company.
Explore the practical operation of Statlook and uplook systems with a completely free webinar. All you need is a chair, an Internet connection and a web browser.
The greatest dangers that banking industry has to encounter are hacker attacks and data leakage. They are usually a result of inefficient IT security procedures. Financial sector is especially difficult to work with, as it heavily relies on clients' trust.
On May 2018 GDPR will be applied within the whole area of the European Union. This document contains a set of rules concerning how to process personal data. It is especially important in banking industry, as its major concern is to prevent data leakage and hacking.
Managing IT infrastructure in a bank cannot consist of loosely tied procedures – mainly because it creates a real threat to the stability of the whole IT environment. The key elements of creating an efficient set of rules are their consistency and completeness.
This is why IT administrators who take care of banking industry ought to invest in a complex IT management system that covers the issues concerning both network and end-users.
While choosing software to support banking industry, we need to inquire whether it has appropriate functions to support and secure IT infrastructure – as well as manage owned resources. It is especially important, as banking is an industry that heavily relies on clients’ trust.
Such a system enables you to manage three main fields of networks:

A current inventory of software and hardware leads to efficient control over IT infrastructure. By doing so, you may rest assured that:
Controlling used memory drivers – by granting authorizations to SSD cards, memory sticks or other media – will vastly minimize data leakage risk.
Software usage monitoring – by controlling how programs, applications and Internet are used during the course of work, an IT administrator can block most vital, dangerous websites and programs.
Statlook guarantees that your IT resources are safe and used according to their destination.
Its complexity allows you to take care about many tasks simultaneously – as such, you need only one program to manage the whole system.
Statlook operates on personal data management in accordance with the rules included in GDPR.
All the factors are the reason of statlook being frequently implemented in public interest entities which operate on data and finances – including banks.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.

In the age of digitalization, IT in education became a worldwide standard. This is why a purchase of an efficient IT management system is an investment – not an expense.
The role of Internet usage and computers in both education process and administration becomes more important. This includes:
* Electronic grade books and schedules,
* E-learning,
* Electronic register systems for both teachers and students.
This phenomenon makes the issue of efficient data management and security even more burning.
It is also important to implement user monitoring in order to ensure network security and data flow control – especially concerning areas exposed to a threat, like:
* Computer studies,
* Libraries with public access to computers and the Internet,
* Auditories
Managing IT infrastructure in education demands a vast effort from administrators.
Duties of an IT administrators include ensuring that each aspect of network efficiency. He is also responsible for the damage caused by the users, data breaches and illegal software – no matter who caused the issue.
This is why the administrators of educational institutions frequently choose systems which supports them and automate their tasks. Complex systems to manage IT networks are one of basic tools of their work. Yet, they should be adjusted to the needs of a company, public institution or educational organization.
Polish institutions most frequently rely on statlook systems – mostly because of its design, created from the scratch with utmost care for both legal demands and our clients’ needs.
Statlook system facilitates IT asset management with three suites:
Statlook Resources – software and hardware inventory,
Statlook Monitoring – user and Internet surveillance,
Statlook Helpdesk – delivering a quick and efficient access to other computers in case an IT incident appears.
Each suite can be configured and joined together according to the needs of an educational facility. Yet, in order to fully control IT infrastructure, it is worth to consider a full suite of the functionalities – a complex statlook system which includes all three suites.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.
Hardware and software inventory is automated – it takes only to remotely install agents on each workstation to gather data about every electronic device that is connected to the network. The data are presented as coherent reports, which can be saved in any format and print, if the situation demands it.
Legality issue looks likewise – it takes only to request a scan of computers to gather data concerning types and number of installed licenses – both commercial and freeware – and educational versions of them. Every function of the system are accessible from the level of Master console.
Monitoring offered by statlook system serves as means of controlling end-users behaviour. The data gathered on an ongoing basis give administrators such pieces of information as:
* Who installed a program and on which workstation,
* Which files and multimedia were downloaded,
* Which websites and domains were visited,
* Which applications were used?
* How much time was spent on a given activity?
This functionality has a key value for IT in education – especially concerning the fact that apart from gaining login reports, an administrator may block access to dangerous or undesirable websites, domains and applications.
This also includes external memory drives – the usage of unauthorized devices also can be blocked or limited to read-only or saving and reading.
This functionality has a key value for IT in education – especially concerning the fact that apart from gaining login reports, an administrator may block access to dangerous or undesirable websites, domains and applications.
This also includes external memory drives – the usage of unauthorized devices also can be blocked or limited to read-only or saving and reading.

Digitalization of health care is a very important issue – especially concerning IT asset management. This process took place long ago – yet because of technical skills and coordination demanded both from IT administration and the personnel, this topic is currently problematic.
This also touches upon the issue of providing a proper level of information security. According to the survey from 2013, approximately one-third of patients were concerned with this aspect of data management; what is more, a survey from 2017 prepared by IBM and Ponemon Institute proved that health-care data breach is the second highest category of threat.
This is why facilities such as hospitals or clinics demand a vast amount of our attention.
Every administrator is aware of the fact that in order to manage IT resources efficiently, it is a key issue to keep hardware and software functional – and every piece of data properly secured. Thus, choosing a system to support administrator’s work should be carefully thought over.
Moreover, it should be remembered that not only does the security play a key value in the case of health-care digitalization – the stability of implemented solutions plays equally important role.

Healthcare demands a complex IT infrastructure management system. It is worth of investing in one, well-rounded program to keep work coherent and efficient.
Statlook equips IT departments with most essential tools:
· Software and hardware inventory,
· Gathering data concerning equipment, license compliance, IT incidents and their history
· Software licensing audit
· Data breach protection
Uncontrolled data flow may lead to their leakage. Such data as the health condition of the patients are considered to be sensitive data, thus this kind of breach is very dangerous – both for them and you, considering legal consequences.
· Ensuring data security is possible to statlook, due to numerous functionalities it is equipped with:
· Internet Control and function of blocking undesirable websites
· Blocking external memory drivers, including memory sticks, SSD cards and removable drives
Statlook Helpdesk suite enables you to remotely connect other computers. It takes only an end-user to report a problem with a piece of equipment or a program via mail or our desktop application. The system creates a ticket which can be ascribed to a person responsible for solving the issue and – if such a necessity appears – request a remote connection. The latter allows an administrator to solve the problem by operating on files or a registry, install or uninstall programs or simply diagnose why the device works improperly.
All the aforementioned functions are only a part of most vital functions of statlook. As you can see, they play a crucial role in IT management – especially considering IT infrastructure in health-care facilities. The system was made from scratch basing on the demands of public trust institutions – so, it is suitable to their characteristics concerning technical condition and legal norms in the EU.
Our technical support is provided by experienced programmers and technicians. We do realize that stability is vastly important in health-care environment. Statlook is a perfect tool to digitalize healthcare.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.
Public administration nowadays becomes more and more reliant on IT-based solutions. It results in technology becoming necessary in an increasing number of branches – including IT infrastructure. What is more, with GDPR entering into force in May 2018, every company that works within the territorry of the European Union will have to carry out new responsibilites.
Modern technologies enhance the fluidity of work within public administration. Because of that, they become a must in an ever-growing, modern society.
Such a facility – as a subject of public confidence – must protect its IT network infrastructure due to responsibilities it is obliged to follow.
There are several standards public administration-related facility ought to follow. It includes:
All these qualities can be checked and measured with a professional IT management system. Because of that, we would like to offer you software which answers your needs.
Explore the practical operation of Statlook and uplook systems with a completely free webinar. All you need is a chair, an Internet connection and a web browser.
User monitoring is an absolute must in every kind of public institution. This kind of surveillance prevents your network from being infected by malware and viruses that would be downloaded from unknown Internet websites.
With a professional IT management solution you can block websites, applications and programs according to your need. Statlook helps you to prevent your facility both from financial loses and legal consequences of jeopardizing your data security.
Efficient work of administration is highly dependant on the condition of your IT infrastructure. Good management and ongoing problem solving is a key to keep everyone's work current.
A well-functioning Helpdesk and remote desktop system integrated into your IT management software is key to provide your workers with necessary support. No matter, how many workers are in IT support department – communication and good problem management will always help you to solve every trouble.
Statlook has all these functionalities. They are integrated into one intuitive interface – in order to make you react even quicker.
IT solutions ought to support everyday tasks of institution of public trust. As a first step to create a balanced organization, they should be considered as a key investment which should be thought over carefully.
Be cautious – your company's public image is at stake. Because of that, let's consider which functionalities are most important for such a system
With this solution, you can efficiently gather information about all IT resources your company owns. It becomes especially easy if such a system can create data record cards. Each change is registered as alerts - also sent via e-mail.
Such module is necessary to check the legality of software owned by the company. It results in safer network and company being able to work in accordance with the law.
Analyze your software, put the licenses in order and implement procedures necessary to enhance the work of administration. The program should detect every attempt of unauthorized installation.
This module should consist of information about used equipment, launched programs and applications as well as visited websites. This range of data enables you to assess the productivity of your workers.
How to speed up IT support in your company? Use software that provides you with current notification registry, ticketing system and remote connection with several computers at once. All the solutions put together create a tool that makes your work easy – and your end-users satisfied with quick servicing.
USB drives, SDD discs and memory cards ought to be controlled in order to prevent key data leakage. It is a component of fully-functional system that enhances security of every kind of company.
Curious to know how your company's equipment is used by the workers? Worried about your data safety? Fear no more – purchase a system which monitors the printing process, including the number of copies, the colour of a printout, its quality as well as who did the printing.
There is always a risk that one of your workers will unintentionally infect your network with a virus from a suspicious website or download. But you can reduce this threat by simply blocking the content.
All the aforementioned functions are provided by statlook system. Consisting of three main modules – Resource, Monitoring and Helpdesk – it is a software that enhances your company's security and overall performance. Each module is available to buy separately - just according to your needs.
Are you interested in checking out its functionalities? Download a free demo version, and become a part of our experience in creating a well-rounded, professional program that will provide every company with wide range of options.
Internet monitoring in work is considered to be one of most important aspects of IT infrastructure management. It is not easy to find an optimal solution, though – not every Internet surveillance system both corresponds with law and remains effective. As statlook is one of most frequently chosen tools in its category, let’s focus on what makes it such a valuable asset.
The screen displayed below shows an example of a report of most frequently visited websites. As you may see, the function of monitoring in statlook does not allow to preview the content of mails, chats or internet websites. Within the report you may only see the headers of websites and portals visited by the users as well as the time spent on it.
Because of that the worker may rest assured that his private data are secured, and the employer can assess the usage of company’s computers using the data gathered within such a report. The time spent on sites and portals will allow you to see if the Internet was used to work or rather to entertain.
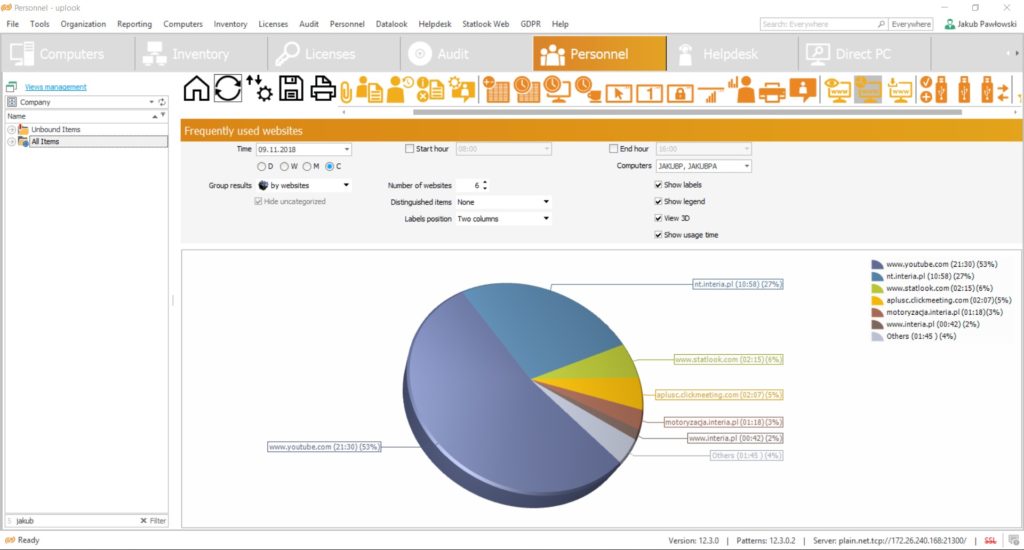
Internet surveillance is one of many functions included within statlook system. Apart from that, statlook enables you to block domains or websites which may be considered to be dangerous (so such ones which may contain viruses) or being a source of cyberslacking (such as social media). Not only will you be able to control if the workers use the Internet according to the code of work, but also you will avoid dangerous incidents. Certain domains and sites might be blocked for individual users or for all organizations.
If workers – in order to handle their duties – need to have access to websites which contain undesirable elements or multimedia, statlook allows you to block their certain ingredients. Because of that, the worker can see the content of such sites without possibility of playing or downloading films, music or software.
Such a solution can be considered as optimal in case if the employee need to use services that are important to his performance – yet might appear to be dangerous for the whole network.
Our clients believe that statlook is a tool well-suited to their demands. They highlight such characteristics as intuitive interface, quick installation and configuration, accordance to current law and possibility of suiting the process of configuration according to a company’s or facility’s individual demands. The tests performed by journalists from a Polish monthly journal IT Professional resulted in statlook gaining a score of 9/10 (the article published in 09/2014 issue). In 2016, statlook was nominated by its readers to be „a product of a year”.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.

Technical support is one of key elements of IT administrators’ daily routine. Because of that, an increasing number of companies and institutions decide to invest into software designed to provide a remote support.
IT administrators are responsible for a variety of tasks – apart from hardware issues, they are also obliged to install software necessary for other workers, protect from viruses and DdoS attacks as well as implementing new programs.
Many companies nowadays also have their structures distributed – so, their localizations usually possess own networks which are controlled by one or two workers. While taking into consideration daily worktime standard and rising demands of supervisors, it is necessary to solve problems in almost real time – and this is why remote support is not a luxury anymore. It is a key tool for every IT administrator to perform their tasks coherently.
Your remote support system should be integrated with IT resource management system – and especially with the helpdesk. This kind of solution both serves as a way to help the end-user instantly and creates a database about IT incidents. With such a solution, you can analyze every problem basing on the history of issues.
We will analyze remote computer access basing on an example of statlook system. It possesses our in-house developed solution – Direct PC. It is an integral part of statlook system and Helpdesk suite.
If an IT incident appears, the user can report it through the application installed on his computer or any other device. The report is instantly aggregated as a ticket within a system. The administrator may describe the status of the issue and the level of priority, and later on assign it to a person who will resolve the problem. Next, if such a need appears, he can connect remotely to the computer via one of three ways – by sending a permission to connect, informing about the time of creating a connection or connecting to the computer in silent mode (without the knowledge of end-user)
After maintaining a connection, the administrator might manage both register and processes from remote, as well as operate on files and catalogues. While doing it, the incident can be analyzed and solved directly through remote desktop. Direct PC enables you to connect with a user both with the authorization of a user of the administrator’s one.
It is especially important because the end-users often find it difficult to describe the moment of the problem appearance or which sequence causes the issue. With this solution, it is easy to recreate the end-user’s logic during issue appearance. Direct PC also serves as a tool to monitor certain groups of computers. Company Online function enables you to remotely preview many workstations in different localizations.
Statlook means more than remote access and helpdesk. It is a full-fledged software to manage IT infrastructure. It takes only to install agents on workstations – also from remote, if you prefer – to gather valuable information about devices, software and users’ activity. An intuitive interface enables you to filter and group data according to your need, as well as create certain reports concerning different elements of IT infrastructure. Our system also allows you to maintain a current monitoring of changes within both software and hardware.
If you would like to see how our system works – including remote access and helpdesk – we would like to invite you to see our free webinar.
The TRIAL version is fully functional for testing in your environment, and we will gladly help you with testing and implementation.

Provided you own a company or work as an IT administrator, and your workers use the Internet on daily basis, it is a wise idea to equip yourself with a program to monitor and block certain websites. Not only will you secure your company’s network - also, you will grasp a valid piece of information on how your workers spend time while surfing on the Web during worktime, yet not necessarily focus on their tasks.
See our explainer video below:
The best solution would be implementing a professional software which both monitors the usage of the Internet and limits the access to undesirable websites – in particular to those which are unverified or commonly known as social media. Such a system, what may be exemplified by the functions provided by statlook, will also ensure that this set of precautions will not be deactivated by end-users.
A program designed to blocking websites and monitoring worktime activity will also successfully limit particularly harmful activities which could jeopardize the security of your company’s network. It takes only to block a website or domain to prevent a user from infecting computers by – often unintentionally - downloading suspicious files or applications. Computer activity monitoring also allows you to identify suspicious website addresses and limit access to them in case they did not happen to be put on a black list.
It depends on a system you use – for example, statlook Monitoring that includes our original weblook module, allows you to control websites frequently visited by the workers and create well-rounded, informative reports on this subject. Moreover, the administrator is informed about the usage of the Interent on a current basis – including websites’ addresses, time spent on browsing them or register of operations done through FTP. Statlook Monitoring also incorporates redirecting to another website address apart from blocking and unblocking them

If workers need to have access to websites that include multimedia content, such as films, photos, games or adverts, the administrator may block access to audio/video files and allow the user to see only the written content on a website. Internet restriction with statlook system may be performed either globally – for the whole company – or locally – for certain departments or even to the users. It is up to administrator of the company’s owner to decide who and how will use the Internet during work time.
Blocking suspicious content and computer monitoring put altogether will allow you to control the network security even better. It will also minimize the risk of infecting your IT infrastructure with viruses or data breach.
With ongoing supervision, reports on visited websites and operations done by the users during their worktime it is easy to check if the workers respect the law and rules of the company.
Programs designed to monitor Internet usage – such as statlook Monitoring – will enable you to limit cyberslacking – which is using the Internet privately during worktime - to a vast extent. Limiting this phenomenon is equal to enhancing workers’ daily performance and the overall effectivity of work.
Experience firsthand how Statlook AI revolutionizes IT management with its comprehensive features and user-friendly interface.